IronPort Web-Security and Cisco ASA 5500 series
2010.02.08
Some nuances I figured out while setting up an IronPort Web-Security appliance with a ASA firewalls. Â The how-tos I’ve seen online were a bit lacking.
It’s easiest to use WCCP to hand-off traffic to the IronPort WSA. Â WCCP requires basically three things to function: Â Which ACLs you want to redirect, where you want to redirect them to, and which WCCP ‘service’ you want to use:
- In ASDM, the standard ACLs can be edited in Firewall | Advanced | ACL Manager
- Create an ACL of IPs you want to (or not) redirect to your WSA. Â Redirect only the TCP/UDP services you want sent to the WSA. Â If you configure ip/any in the ACL, then all packets will get sent over to the WSA. Â This seems to break ICMP. Â Do this through the GUI or from the CLI. Â Some http-based apps don’t like this redirection so putting a ‘deny’ at the top of the ACL works.
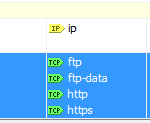
- Create another ACL of your IronPort WSAs. Â I think these need to be on the same subnet as the WCCP is happening (multicast and all). Â i didn’t try putting the WSA on a separate interface than the ASA, nor did i try it with multicast routing enabled between them either.

- Third, we need to configure the redirection, and which interfaces the ASA listens to for WCCP. Â In the GUI, Device Management | Advanced | WCCP. Â Create a Service Redirection first. Â This binds which IPs get to which WSAs. Â Leave it on Web Cache for the simplest configuration. Â I tried setting a password but that seemed to break WCCP. Â (See notes below)
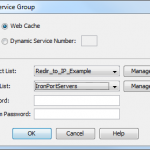
The ‘redirection’ binds which interface the ASA listens for WCCP on.
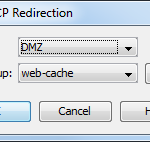
- Lastly, don’t forget to set up ACLs so your WSAs can access the internet
- configuring the WSA-end of things is straight forward. Â following the instructions from the help menu is about all you need.
Notes:
- So far, I’ve only worked with the WSA 6.3.x code tree.
- About policy matching: Â Identity Polcy matches first. Â Whether it’s IP or authentication based, first rule wins. Â Take the matching Identity Policy that won and match it to the first Access Policy. Â Then applications, URL categories, objects, etc.
- As of ASA code 8.2.1, WCCP load balancing is only hash-based. Â There’s no way to change it to (subnet) mask balancing. Â if you need mask balancing, use an IOS-based device for now.
- As of ASA code 8.2.1, any time you apply policy on the WSA (update access lists, identities, anything at all, really) you need to re-apply the service group (step 4); delete the policy, apply it. Â create the policy and apply it.
- The redirection password may be an issue with re-applying WSA policies. Â We’re in production now so I haven’t taken it down to play.
- If you use a ‘warning’ page for suspect URL categories (streaming media, social networking, etc) and you have hash-based load balancing, the users will get warned from each WSA you have load balanced
- At this time, there’s no central management for multiple WSAs. Â If you change policy on one WSA, you need to apply it to the other manually.
